RCO: Process Hollowing
| Target OS | Demo |
|---|---|
| Linux |  |
| Windows |  |
How it works
Windows process hollowing works by creating a suspended process and writing the shellcode over the entry point of the process’s main thread. It then resumes the suspended process, which in turn executes the shellcode.
Linux process hollowing functions a little differently. First, the executable creates a child process by cloning itself. Then it overwrites the child process’s instruction pointer with shellcode. Because this process was not running before the attack, it is unlikely this will cause any issues on the victim machine.
Using it
- [Not shown in demo] Generate shellcode for the desired end result (for example, use msfvenom to generate a reverse TCP shell shellcode for the target operating system)
- [Not shown in demo] Open the config file and change the shellcode to the shellcode generated in step 1
- [Optional - shown in xor_params demo] Encrypt the shellcode and target process using xor_params and update the encrypted shellcode value in the config file
- [Not shown in demo] Compile the executable, only including
--features xorif you did step 3- Build for Linux target
cargo build -p process_hollowing [antisand][,][antistring][,][xor]] --release - Build for Windows target
cargo build --target x86_64-pc-windows-gnu -p process_hollowing [antisand][,][antistring][,][xor]] --release
- Build for Linux target
- Start a netcat listener on the attacking machine on the same port you configured the shellcode to connect to in step 1
nc -nlvp 4444 - Execute the payload on the victim machine
- Return to the listener and enter desired commands for the victim machine to run
Detection rates
| Target OS | Features | Detections | Screenshot |
|---|---|---|---|
| Linux | None | 7 / 40 | 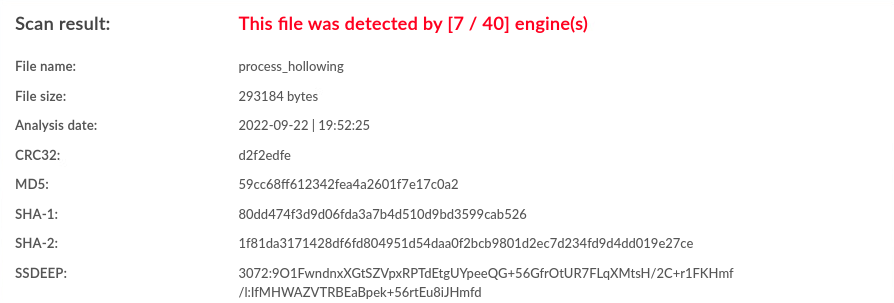 |
| Linux | xor |
1 / 40 | 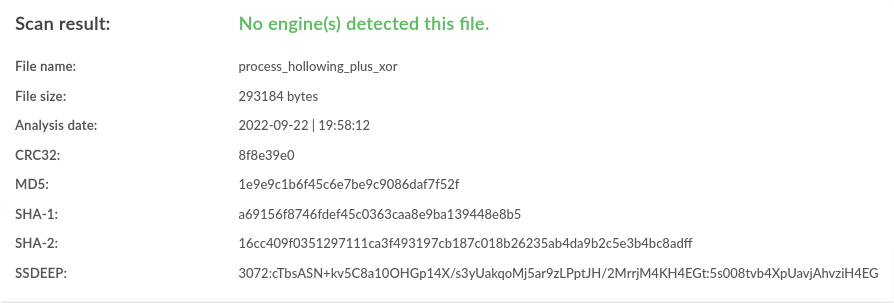 |
| Windows | None | 12 / 40 | 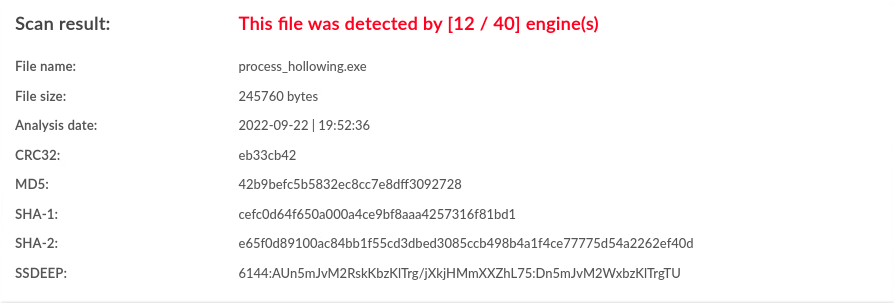 |
| Windows | antisand |
11 / 40 | 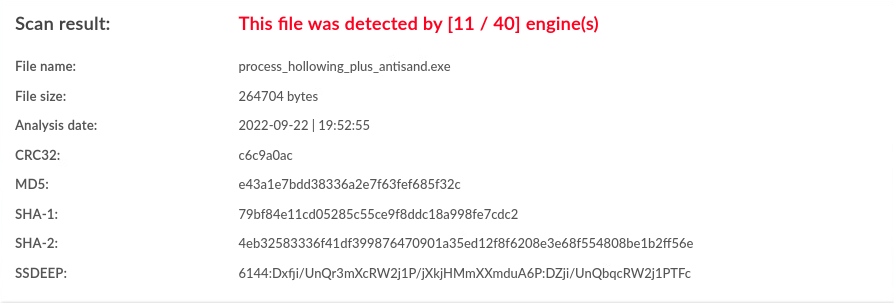 |
| Windows | antisand,antistring |
11 / 40 | 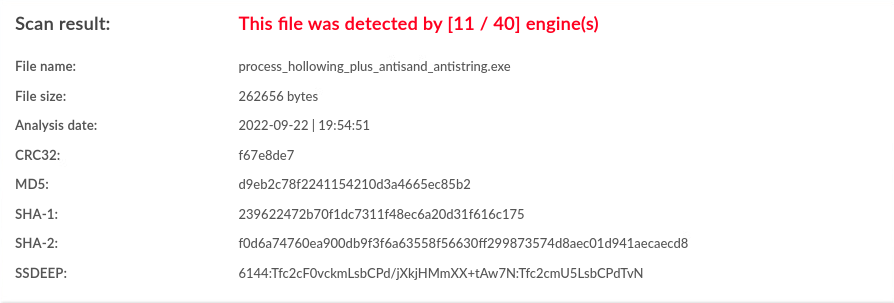 |
| Windows | antistring |
11 / 40 | 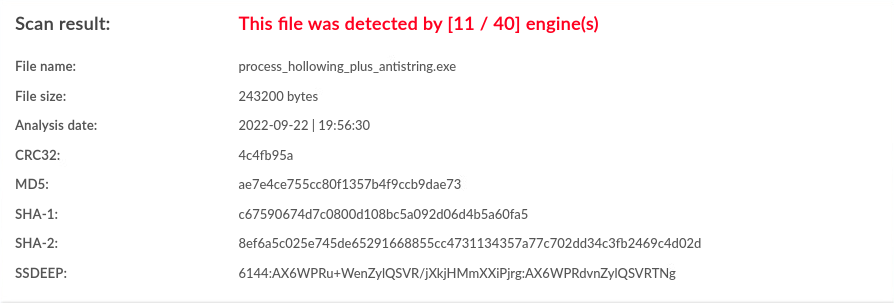 |
| Windows | antistring,xor |
1 / 40 | 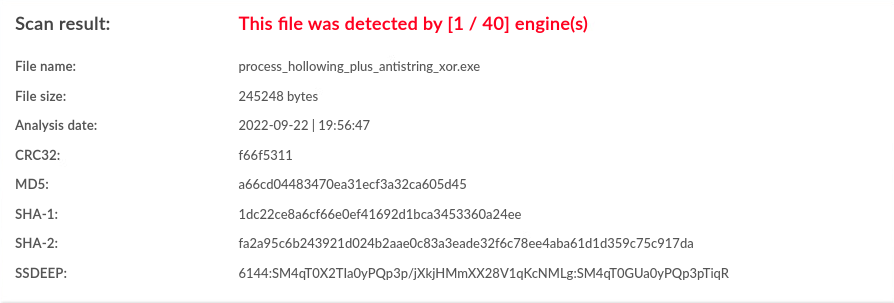 |
| Windows | xor |
1 / 40 | 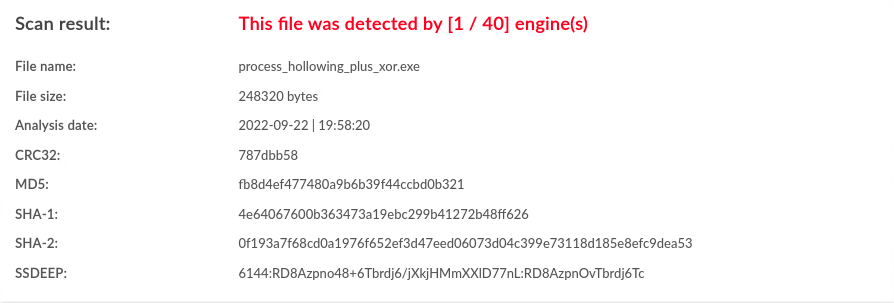 |
| Windows | antisand,xor |
0 / 40 | 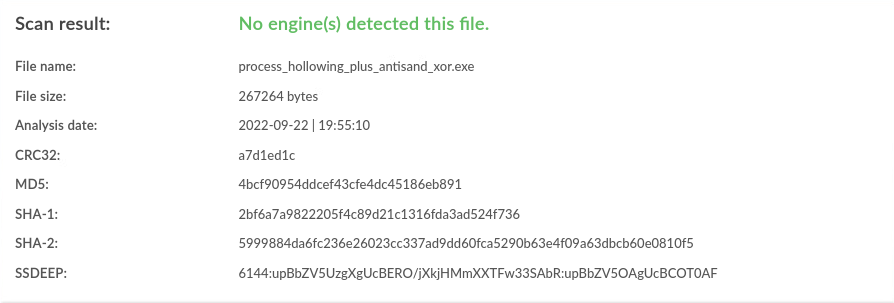 |
| Windows | antisand,antistring,xor |
0 / 40 | 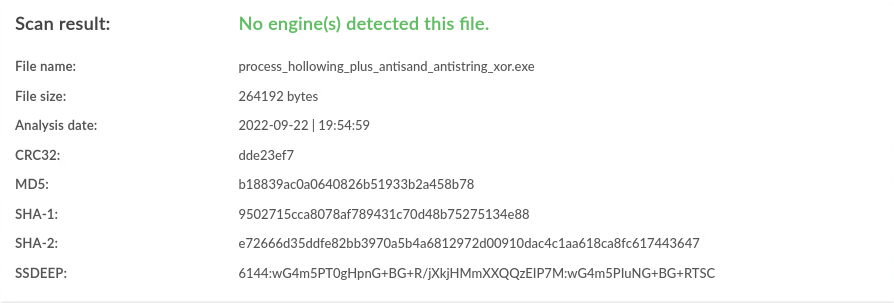 |
